Can ChatGPT's Multimodal Image Recognition Crack CAPTCHAs?
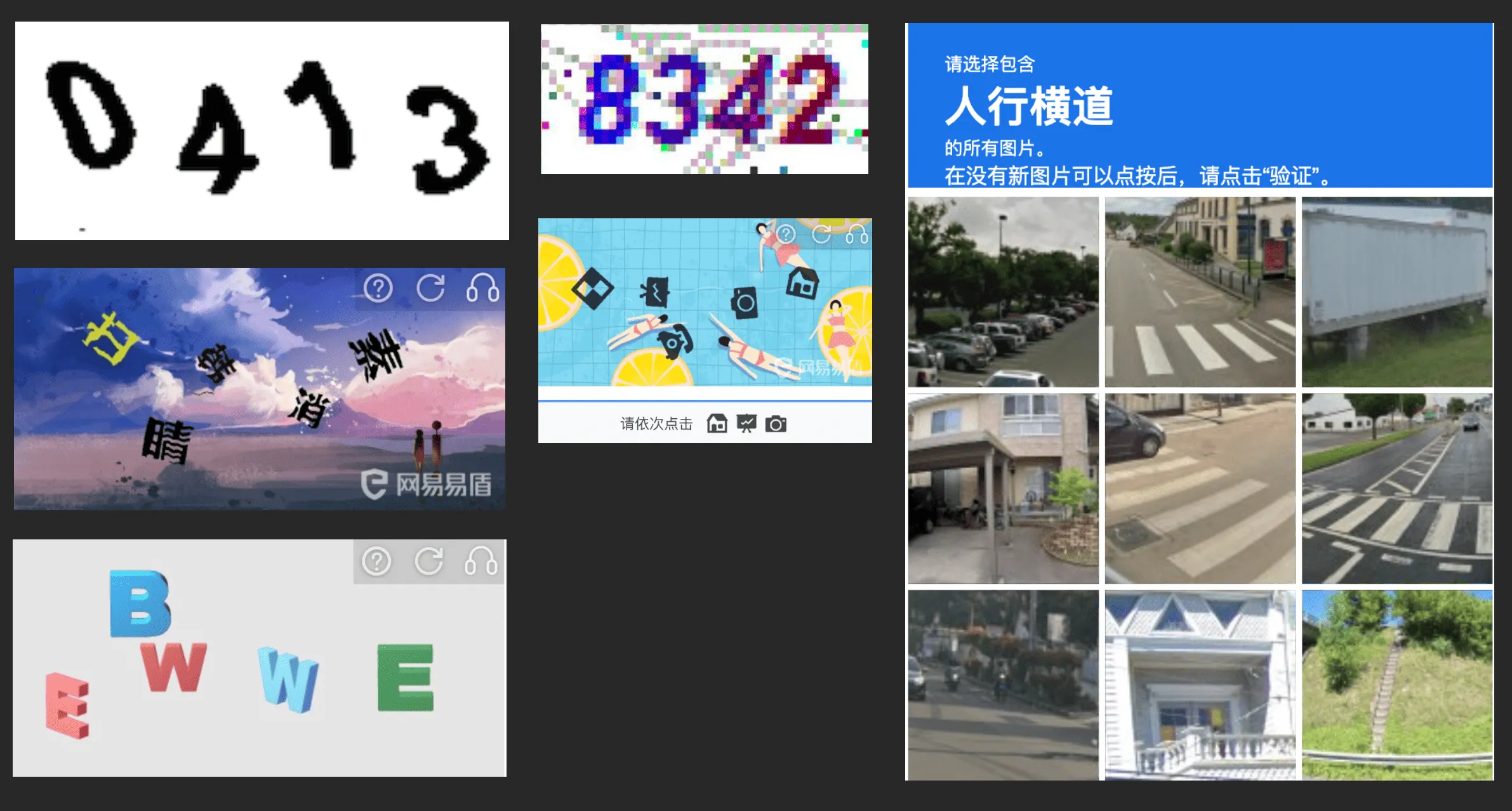
CAPTCHAs have become an indispensable part of our daily online lives, providing a basic security barrier for websites and applications. From the initial simple numerical CAPTCHAs to various complex ones today, their complexity has been gradually increasing to resist attacks from automated tools and bots.
The following image shows some common CAPTCHAs:
The sole purpose of these CAPTCHAs is to distinguish between humans and machines. However, with the rise of large models like ChatGPT, especially the advent of GPT4-Vision’s multimodal capabilities, can CAPTCHAs still intercept machines?